rfid tag copy protection By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack that will steal sensitive information or breach secured areas.
Here is how the “Handheld RFID Writer” (that you can easily purchase for less than $10) works: Turn on the device. Hold a compatible EM4100 card or fob to the side facing the hand grip and click the ‘Read’ button. The .
0 · nfc tags not copying
1 · nfc tags block copying
2 · nfc tag protection
3 · intrinsic id vs rfid
4 · intrinsic id rfid tag
5 · how to prevent rfid tag cloning
6 · how to block rfid tags
Copying NFC card on phone . I have a question and would be thrilled if someone would know the answer. I have a NFC card that I have to use on the job and broke 2 already so is there a way .
NXP Semiconductors has incorporated PUF technology into its SmartMX2 ICs (see RFID News Roundup: NXP Strengthens SmartMX2 Security Chips With PUF Anti-cloning Technology). Another way is to use an RFID tag that supports encryption technology. RFID tags can be cloned. Tags which do not make use of password-protection or over-the-air (OTA) encryption can have their data banks copied into new tags. RFID tags (at .NXP Semiconductors has incorporated PUF technology into its SmartMX2 ICs (see RFID News Roundup: NXP Strengthens SmartMX2 Security Chips With PUF Anti-cloning Technology). Another way is to use an RFID tag that supports encryption technology. RFID tags can be cloned. Tags which do not make use of password-protection or over-the-air (OTA) encryption can have their data banks copied into new tags. RFID tags (at least Class 1 Generation 2 tags, aka UHF RFID tags) are computationally active, not passive.
NFC tags (as defined by the NFC Forum) have no protection against cloning. Such tags are intended as containers for freely readable data (so called NDEF messages). Anyone could read an NDEF message from one tag and duplicate it to another tag. By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack that will steal sensitive information or breach secured areas.
There are two general strategies to pro-vide security: prevention and detection. The security community and the RFID chip manufacturers are currently focused on the former by making tags hard to clone. This paper focuses on the latter by investigating a method to .Each RFID chip has a unique serial number that cannot be changed, which identifies the chip as unique. A serial number is then written to the tag’s memory. You could read the TID and serial number and make sure there was a correct match, in order to ensure the tag was not cloned. Today, we’re going to show you how easy it is to make an RFID clone and an NFC clone, talk about the best ways to thwart black hats that are after your cards, as well as touch on what you do when you legitimately need RFID cloning. In this paper, we conduct the first comprehensive and systematic survey of RFID clone prevention and detection solutions. We systematically classify existing RFID cloning countermeasures over the period 2003–2016, sketch the main idea and highlight the strengths and weaknesses of each solution type, and summarize the similarity and difference .
Eavesdropping occurs when someone uses a receiver to pick up on this conversation which happens out in the open. Without proper protection, this receiver could steal data during a legitimate exchange between a tag and reader. So, how can you protect your information from these threats? 1. SwitchesRFID cloning involves the unauthorized copying of legitimate RFID tags to gain access to restricted areas or valuable assets. Hackers can use specialized equipment to read the information stored on a legitimate tag and then create a duplicate tag with the same information.NXP Semiconductors has incorporated PUF technology into its SmartMX2 ICs (see RFID News Roundup: NXP Strengthens SmartMX2 Security Chips With PUF Anti-cloning Technology). Another way is to use an RFID tag that supports encryption technology. RFID tags can be cloned. Tags which do not make use of password-protection or over-the-air (OTA) encryption can have their data banks copied into new tags. RFID tags (at least Class 1 Generation 2 tags, aka UHF RFID tags) are computationally active, not passive.
NFC tags (as defined by the NFC Forum) have no protection against cloning. Such tags are intended as containers for freely readable data (so called NDEF messages). Anyone could read an NDEF message from one tag and duplicate it to another tag.
nfc tags not copying

nfc tags block copying
By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack that will steal sensitive information or breach secured areas.There are two general strategies to pro-vide security: prevention and detection. The security community and the RFID chip manufacturers are currently focused on the former by making tags hard to clone. This paper focuses on the latter by investigating a method to .
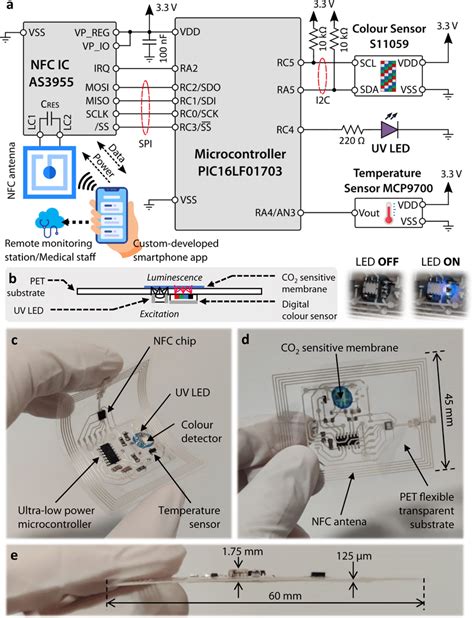
Each RFID chip has a unique serial number that cannot be changed, which identifies the chip as unique. A serial number is then written to the tag’s memory. You could read the TID and serial number and make sure there was a correct match, in order to ensure the tag was not cloned.
Today, we’re going to show you how easy it is to make an RFID clone and an NFC clone, talk about the best ways to thwart black hats that are after your cards, as well as touch on what you do when you legitimately need RFID cloning. In this paper, we conduct the first comprehensive and systematic survey of RFID clone prevention and detection solutions. We systematically classify existing RFID cloning countermeasures over the period 2003–2016, sketch the main idea and highlight the strengths and weaknesses of each solution type, and summarize the similarity and difference . Eavesdropping occurs when someone uses a receiver to pick up on this conversation which happens out in the open. Without proper protection, this receiver could steal data during a legitimate exchange between a tag and reader. So, how can you protect your information from these threats? 1. Switches

nfc tag protection

what do i need to make a smart card id
$22.99
rfid tag copy protection|intrinsic id vs rfid