is nfc tag reader safe iOS will not read data from an NFC tag without an app. Once the app is downloaded and granted permission, background reads are still possible, but for doing internal things (such as toggling the flashlight) iOS does not provide access. Tried on two different tablets then reloaded Windows 10 but sill no card is ever .NFL Playoff Picture. Stay up to date with your favorite team to see if they have a chance to make the 2024 playoffs. Seven teams from each conference will make it to the postseason. Check out .
0 · what does nfc tag mean
1 · nfc tags explained
2 · nfc tag detected meaning
3 · how to use nfc tags
4 · how far does nfc reach
5 · examples of nfc tags
6 · different types of nfc tags
7 · are nfc tags rewritable
The Auburn Tigers were the 28-20 winners over the Texas A&M Aggies when they previously met last September. Saturday? They had no such luck. The Tigers came up short against A&M, falling 31-20..
what does nfc tag mean
Data interception presents a significant security risk by exposing the private information of two NFC users. If a criminal launches an attack within the range of two devices using NFC communication, the attacker can intercept communication signals and easily record the data being broadcast. Relying on physical access to a device to authenticate someone’s identity is risky, however, because it means that a person who steals an NFC tag or security key could gain unauthorized access to places and systems protected by the stolen device.
nfc tags explained
NFC tags are also vulnerable to tampering. For example, users have tapped smart tags thinking they were about to access movie trailers or visit a vendor website but instead had their.
iOS will not read data from an NFC tag without an app. Once the app is downloaded and granted permission, background reads are still possible, but for doing internal things (such as toggling the flashlight) iOS does not provide access.
NFC tags and readers communicate wirelessly with each other over very short distances. Tags store a small amount of data on them that is sent to the reader in the form of electromagnetic.
Smart tags are tiny, read-only chips that can appear in informational posters and identification documents, such as corporate badges or passports. You can even use NFC to connect to secure networks without having to enter complex authorization codes.
A compromised NFC tag or device could be used to deliver malware to an unsuspecting user’s device. If a user’s device is set to read NFC tags automatically, the device could be infected simply by getting too close to a malicious tag.Any powered device that has its own NFC coil (like a smartphone or tablet) can act as an NFC reader. The reader device uses its battery to generate an electromagnetic field, which powers any.
Quick Links. What Is NFC Used For? Do All Android Phones Have NFC? How to Turn On NFC on Android. How to Use Programmable NFC Tags on Android. How to Turn Off NFC on Android. Key Takeaways. NFC stands for "Near Field Communication," and it enables devices to communicate wirelessly over a short distance.
nfc tag detected meaning
Is NFC tag safe? NFC tags are generally considered to be safe and secure. They have a unique UID (Unique Identifier) that cannot be easily duplicated, ensuring their authenticity. Data interception presents a significant security risk by exposing the private information of two NFC users. If a criminal launches an attack within the range of two devices using NFC communication, the attacker can intercept communication signals and easily record the data being broadcast. Relying on physical access to a device to authenticate someone’s identity is risky, however, because it means that a person who steals an NFC tag or security key could gain unauthorized access to places and systems protected by the stolen device. NFC tags are also vulnerable to tampering. For example, users have tapped smart tags thinking they were about to access movie trailers or visit a vendor website but instead had their.
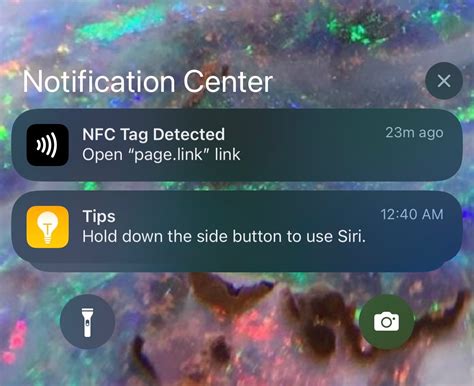
iOS will not read data from an NFC tag without an app. Once the app is downloaded and granted permission, background reads are still possible, but for doing internal things (such as toggling the flashlight) iOS does not provide access. NFC tags and readers communicate wirelessly with each other over very short distances. Tags store a small amount of data on them that is sent to the reader in the form of electromagnetic.Smart tags are tiny, read-only chips that can appear in informational posters and identification documents, such as corporate badges or passports. You can even use NFC to connect to secure networks without having to enter complex authorization codes.
A compromised NFC tag or device could be used to deliver malware to an unsuspecting user’s device. If a user’s device is set to read NFC tags automatically, the device could be infected simply by getting too close to a malicious tag.
Any powered device that has its own NFC coil (like a smartphone or tablet) can act as an NFC reader. The reader device uses its battery to generate an electromagnetic field, which powers any.
Quick Links. What Is NFC Used For? Do All Android Phones Have NFC? How to Turn On NFC on Android. How to Use Programmable NFC Tags on Android. How to Turn Off NFC on Android. Key Takeaways. NFC stands for "Near Field Communication," and it enables devices to communicate wirelessly over a short distance.
rfid tag sample

how to use nfc tags
how far does nfc reach
examples of nfc tags
Our monthly club meetings will resume in 2025, on January 10 at 7:30 PM at the Confluence (formerly Crossroads) Church Gym in Auburn, California and on Zoom at zoom.w6ek.org. Serving amateur radio operators throughout the Sierra Nevada Foothills and beyond since 1958.
is nfc tag reader safe|are nfc tags rewritable