rfid chip security issues RFID chipsare becoming increasingly popular for tracking people and products, but they can also raise serious privacy concerns. The technology is essentially invisible, allowing for . See more Ever wanted to add your most used NFC Cards to Wallet on your phone? Introducing Aemulo. Aemulo allows you to read, write and emulate tags from one app. It also has the ability to add cards to Wallet so you can invoke them .
0 · what is rfid technology
1 · what is rfid security
2 · rfid security threats
3 · rfid security problems
4 · rfid credit card check
5 · rfid credit card
6 · rfid card logo
7 · is my rfid card safe
An Android Library to read info from NFC enabled cards. Note - This library does not log or send any of the sensitive card information. All processing is done on the device. Inspired from EMV-NFC-Paycard-Enrollment and Credit-Card-NFC .There are many hardware features that can be important when choosing a credit card reader. However, the most important feature is compatibility with your Android device. The reader should connect to your device easily and be able to process payments quickly. Other hardware features that can be important . See more
RFID chips, or Radio Frequency Identificationchips, are small electronic devices that use radio waves to store and transmit data wirelessly. These tiny devices have a wide range of applications, from tracking products and assets to providing access control. RFID tagging involves the use of small devices that transfer data . See moreRFID chips can be a great asset, but they also come with a number of potential risks and dangers. Environmental factors are the most commoncause of RFID interference problems. While there are some benefits of using RFID tags for inventory . See moreRFID chipsare becoming increasingly popular for tracking people and products, but they can also raise serious privacy concerns. The technology is essentially invisible, allowing for . See moreRFID technologyhas been increasingly implemented in the healthcare sector, with the aim of improving patient safety and increasing its impact. . See more
RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data. Additionally, . See more
A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and . Security Risks. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data. Additionally, RFID systems are susceptible to passive eavesdropping as well as . A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a .Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed properly before deployment. This post aims to highlight several important RFID related security issues.
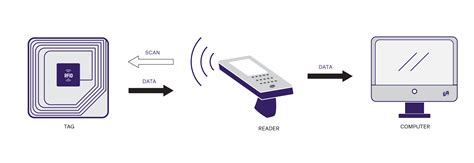
RFID credit cards are considered to be as safe as EMV chip cards, and data theft concerning RFID cards is uncommon. This is because of how these cards transmit information and what information is. The main security issue associated with the use of RFID systems is that they are susceptible to attacks or viruses from hackers and fraudsters. However, there is comfort in knowing that attacks on RFID systems aren’t easy to penetrate. These chip-based contactless cards have been targeted by various attacks over the years and remain vulnerable despite the introduction of updated versions. In 2020, Shanghai Fudan released a.There are two primary areas where RFIDs raise privacy issues: their use in retail and elsewhere in the commercial sector, and their direct adoption by government. In both cases, RFID tags make it possible for governments, stores, and hackers to identify people at .
kodak smart card review
“Security issues in RFID system” presents various attacks possible on RFID devices. This section includes the attacks based on the CIA (confidentiality, integrity, and availability) properties of the RFID system. This report on RFID chip-level security is written to help both technical and non-technical audiences navigate the complex chip-level security features of RFID smart cards and tags, and make intelligent security choices. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.
Security Risks. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data. Additionally, RFID systems are susceptible to passive eavesdropping as well as . A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a .Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed properly before deployment. This post aims to highlight several important RFID related security issues.
RFID credit cards are considered to be as safe as EMV chip cards, and data theft concerning RFID cards is uncommon. This is because of how these cards transmit information and what information is.
The main security issue associated with the use of RFID systems is that they are susceptible to attacks or viruses from hackers and fraudsters. However, there is comfort in knowing that attacks on RFID systems aren’t easy to penetrate. These chip-based contactless cards have been targeted by various attacks over the years and remain vulnerable despite the introduction of updated versions. In 2020, Shanghai Fudan released a.There are two primary areas where RFIDs raise privacy issues: their use in retail and elsewhere in the commercial sector, and their direct adoption by government. In both cases, RFID tags make it possible for governments, stores, and hackers to identify people at . “Security issues in RFID system” presents various attacks possible on RFID devices. This section includes the attacks based on the CIA (confidentiality, integrity, and availability) properties of the RFID system.
This report on RFID chip-level security is written to help both technical and non-technical audiences navigate the complex chip-level security features of RFID smart cards and tags, and make intelligent security choices.
what is rfid technology
what is rfid security
java smart card pkcs11
Custom NFC digital business cards make a bold impression. Tap to share your contact info in seconds. Pick from a card, metal design, or bracelet—each comes with a QR code for quick sharing. . and virtual tour videos. This essential tool .Introducing VistaConnect – a free service that adds an online extension to a single business card you keep. Smart scanning technology instantly brings customers to schedules, signup forms and everything else that makes your business go. See our guide. See more
rfid chip security issues|is my rfid card safe